Virtual Private Networks (VPNs) are a way to securely connect two or more computers across an otherwise insecure connection.
Example: I bring my computer to my local coffeeshop to work on my list of the greatest episodes of the 1989 animated tv show Captain N: The Game Master…but I saved the list on my home computer and forgot to copy it to my laptop! I dare not connect to my home on the coffeeshop wifi network; it is completely insecure and open to any malicious actor that can run a Packet Sniffer. How can I securely connect across an insecure network to my home computer?
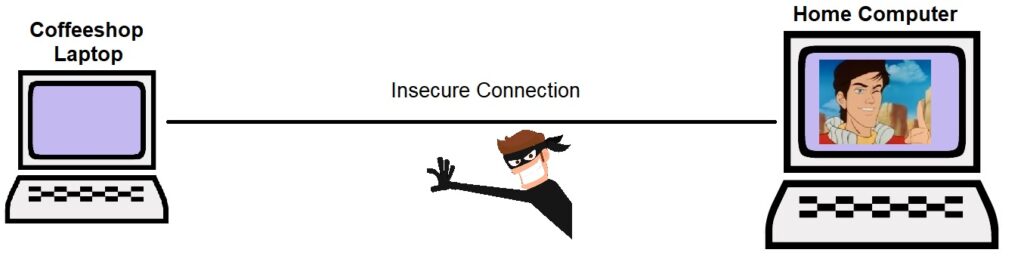
This is a perfect situation to implement a VPN. The VPN creates a secure tunnel inside the insecure connection. At a more more detailed level, VPNs actually wrap the data in very strong encryption, so that if the Data Thief™ gets the data, he would be unable to read it or do anything with it. The encrypted data travels all the way across the insecure connection, and only get decrypted once it arrives safely at the other end.
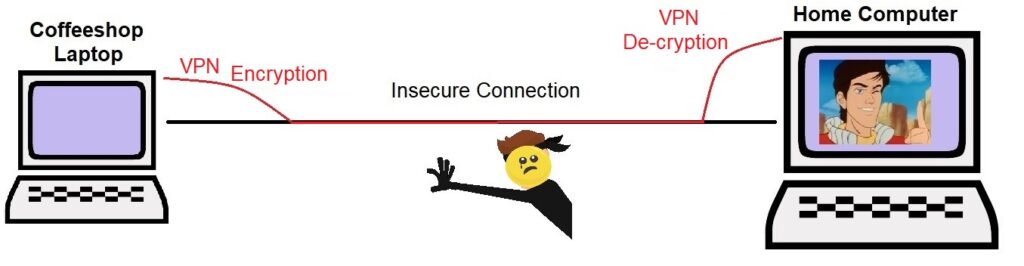
Now, the laptop (which we’ll call the VPN client) and the home computer that has the desired data (which in this case, is the VPN server) can be implemented by a program that runs on your computer, by the operating system itself (Windows, Linux, etc.), or by dedicated hardware such as a switch or router. What is most important, and most difficult, is making certiain that the client and server are using the same encryption and decryption tools so that their “handshake” matches.